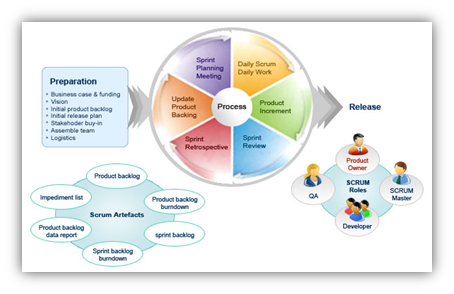
We use Scrum based software development process. We can also adapt to client processes and tools when required. Products are developed in incremental way in order to maintain flexibility for changing requirements and to provide best possible visibility to project status.
Development is broken down to fixed length 'Sprints', which are typically two weeks in duration. Client is provided with a release at the end of each sprint for verification and feedback